Module
Turn network reality into audit-ready truth.
Command is the operational layer for collectors, telemetry, data quality, and evidence. It doesn’t just ingest data. It proves your integration is correct and guides remediation when it’s not.
Field CoverageEncrypted snapshotsAudited actionsRBAC
Built for teams who must prove network posture
- Regulated environments needing defensible telemetry and config evidence
- Teams consolidating SIEM and network data collection
- Anyone tired of “it’s probably working”
Not required for every customer.
Command is modular and can be disabled. Enable only what you need for your program.
auroracommand.ai / Command Overview
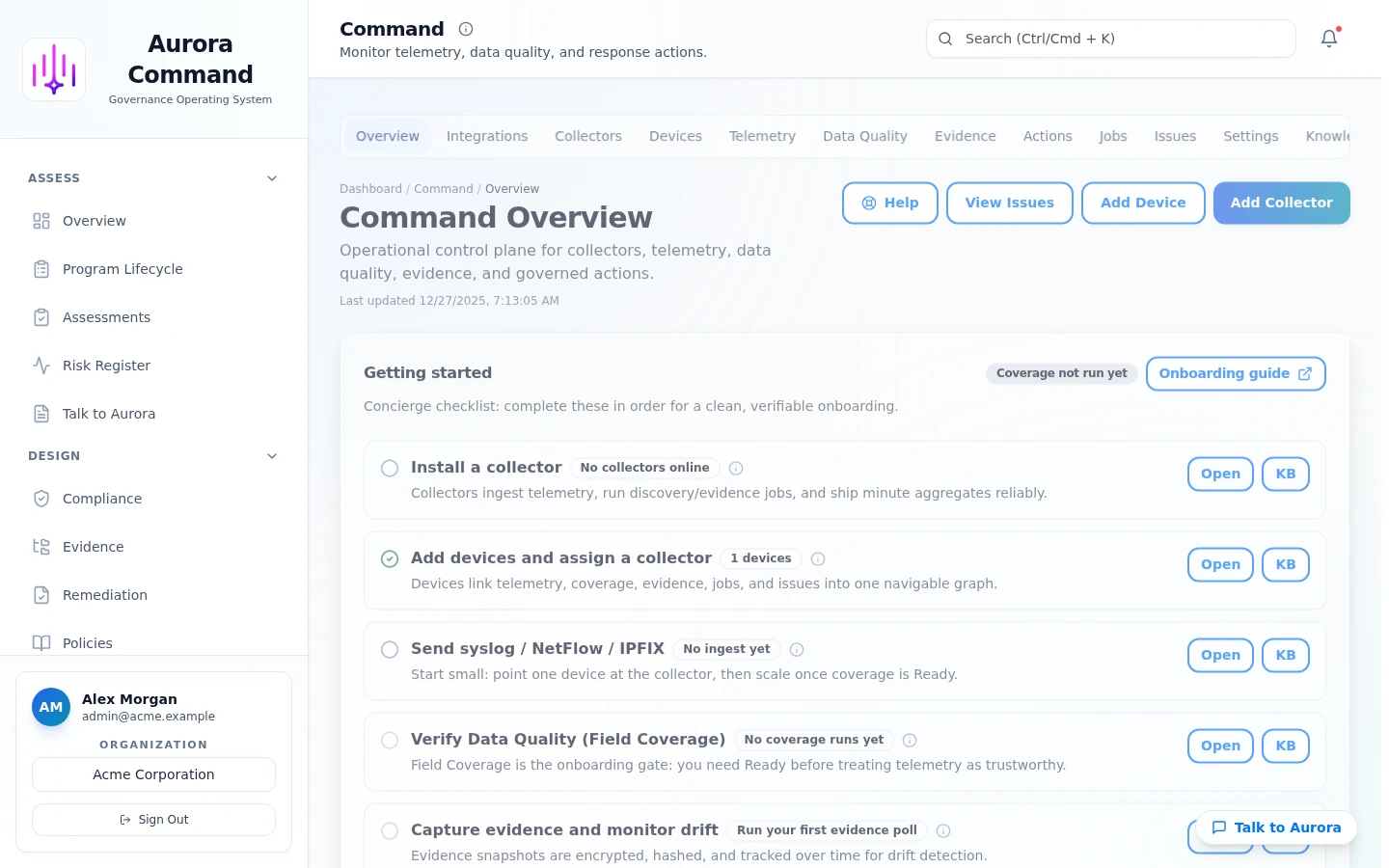
Real product UI.
What it does today
Current capabilities, formatted for clarity.
Collectors with disk spooling, backpressure, retries
Syslog + NetFlow v9 + IPFIX ingestion with normalization
Field Coverage verdicts (Ready / Needs Config / Parser Mismatch / No Data)
Encrypted evidence snapshots with hashes + drift detection
Governed actions with plan/apply/rollback + approvals
RBAC enforced everywhere
Artifacts produced
Designed to be exportable, attributable, and defensible.
Where Command is going
Command is expanding toward unified security telemetry and governed configuration evidence across SIEM and network controls.
Remote collectors for SIEM event gathering
Roadmap: we’ll walk you through fit and scope on a demo. Enable only what you need.
Firewall and network device configuration evidence workflows
Roadmap: we’ll walk you through fit and scope on a demo. Enable only what you need.
Guided onboarding playbooks per data source
Roadmap: we’ll walk you through fit and scope on a demo. Enable only what you need.
Tech details
Built for defensibility and performance
Storage architecture (evidence object store + integrity hashes)
Storage architecture (evidence object store + integrity hashes)
Snapshots are stored as evidence objects with integrity hashes and drift detection so you can prove what existed at a point in time.
Performance model (minute aggregates, ClickHouse)
Performance model (minute aggregates, ClickHouse)
Telemetry workflows are designed for high-throughput ingestion and efficient analytics via ClickHouse-backed aggregates.
Security model (TLS, RBAC, audit logs, kill switch)
Security model (TLS, RBAC, audit logs, kill switch)
Secure transport, role-based permissions, audited actions, and the ability to disable remote actions when needed.
If you can’t prove it, it doesn’t count.
See how Command turns telemetry correctness into exportable technical proof.